Russia escalates phishing attacks with sophisticated tactics
 Russian flag displayed in a screen. (Photo via Getty Images)
Russian flag displayed in a screen. (Photo via Getty Images)
Russia’s state security agency is reportedly launching increasingly sophisticated phishing attacks against members of civil society in the U.S., Europe, and even within Russia itself.
These attacks, which are part of a broader state-sponsored hacking campaign, have been evolving in both social engineering strategies and technical aspects, according to a new investigation by security researchers.
Rising sophistication in Russian phishing campaigns
A recent report from the Citizen Lab at the University of Toronto and Access Now reveals that the Russian Federal Security Service (FSB) has been behind a series of highly advanced phishing attacks. These campaigns have not only targeted former U.S. officials but also prominent Russian opposition figures in exile, journalists, and human rights activists.
One of the most striking aspects of these attacks is their use of social engineering. In some cases, the hackers impersonate individuals who are personally close to the targets, making the phishing attempts much harder to detect. This marks a significant evolution in the tactics employed by Russian state-sponsored actors, moving beyond traditional methods to more intricate and convincing schemes.

High-profile targets
Among the recent targets are Steven Pifer, the former U.S. ambassador to Ukraine, and Polina Machold, an exiled Russian publisher. Pifer was targeted through a “highly credible” exchange that involved someone impersonating another former U.S. ambassador he knew. This deceptive approach underscores the increasing sophistication of these attacks, as they leverage personal relationships to gain trust.
Polina Machold, who now resides in Germany after being expelled from Russia in 2021, was also targeted in a particularly sophisticated manner. In November 2023, she received an email from someone posing as a counterpart at another publishing house she had previously worked with. Although the initial email appeared to be a routine communication, it raised suspicions when a follow-up email, sent from a Proton Mail account, included an attachment that required her to input her login details. After contacting her colleague directly, she realized the emails were fraudulent.
Machold expressed her concern about the advanced nature of the attack, stating, “I had not seen anything like this before. They knew I had contacts with this person. I didn’t have a clue even though I consider myself to be on high alert.”
Role of threat actors Coldriver and Coldwastrel
Researchers identified the primary threat actor behind these attacks as a group they dubbed “Coldriver” which has been linked to the FSB by multiple governments. A second threat actor, known as “Coldwastrel” has displayed similar patterns in its targeting, focusing on individuals and organizations of interest to the Russian state.
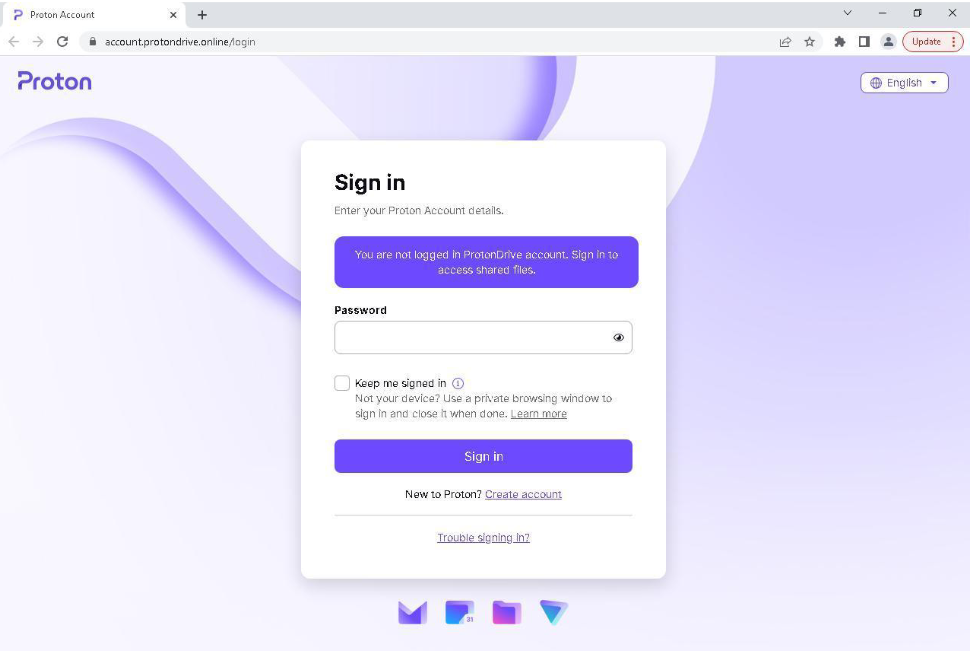
These groups have employed a common tactic: initiating an email exchange with the target while masquerading as someone the target knows. The attackers typically request the target to review a document, which is attached as a PDF that appears to be encrypted using a privacy-focused service like Proton Drive. The email may even include a login page pre-populated with the target’s email address, making the phishing attempt appear legitimate. If the target enters their credentials, the attackers gain immediate access to their email accounts and any linked online storage.
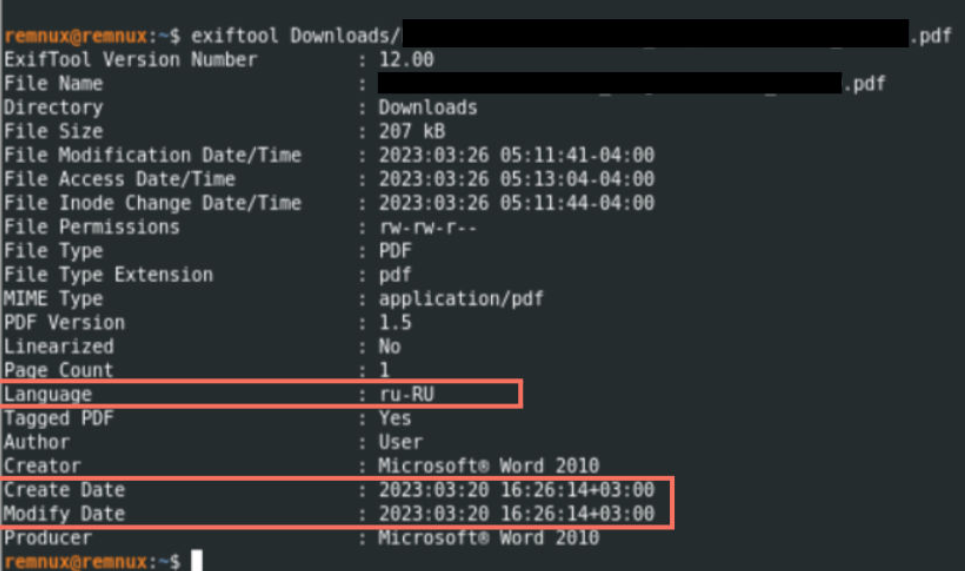
language (ru-RU).
Significant risks
The implications of these phishing campaigns are severe, particularly for individuals and organizations involved in sensitive activities. Rebekah Brown, a senior researcher at the Citizen Lab, emphasized the potential dangers: “As soon as these attackers get credentials, we think they will work immediately to access email accounts and any online storage, like Google Drive, to pull as much sensitive information as they can. There are immediate risks to life and safety, especially if information concerning people still in Russia is in those accounts.”



